Network Integration
WAN Network Solution
We Design a Wide Area Network (WAN) solution is essential for organizations that need to connect multiple sites or branch offices over long distances. A well-designed WAN allows for efficient data communication, collaboration, and resource sharing across geographically dispersed locations.
Here are the key considerations when planning a WAN network solution:

-
Network Topology:
- Determine the WAN topology that best suits your organization's needs. Common WAN topologies include point-to-point, hub-and-spoke, full mesh, and hybrid combinations.
-
Network Connectivity:
- Choose the appropriate network connectivity options based on your requirements. This may include leased lines (T1, T3, E1, E3), Multiprotocol Label Switching (MPLS), broadband internet, Virtual Private Networks (VPNs), or dedicated fiber connections.
-
Routing and Routing Protocols:
- Select routing equipment and protocols (e.g., BGP, OSPF, EIGRP) to efficiently route traffic between WAN sites while considering factors like reliability and redundancy.
-
Quality of Service (QoS):
- Implement QoS policies to prioritize critical traffic, such as voice and video, over less time-sensitive data to ensure optimal performance.
-
Bandwidth Management:
- Monitor and manage bandwidth to allocate resources effectively and address congestion issues.
-
Network Security:
- Implement robust security measures, including firewalls, intrusion detection/prevention systems (IDS/IPS), encryption, and access control, to safeguard data during transit.
-
Redundancy and Failover:
- Design the WAN with redundancy to minimize downtime. Implement failover mechanisms to automatically switch to backup connections in case of primary link failures.
-
WAN Optimization:
- Employ WAN optimization solutions to accelerate data transfer and application performance over long distances. These solutions can reduce latency and bandwidth utilization.
-
Traffic Management and Load Balancing:
- Use traffic management and load balancing solutions to distribute network traffic evenly across multiple WAN links, optimizing performance and reliability.
-
Remote Access Solutions:
- Provide secure remote access solutions like VPNs or DirectAccess for remote users to connect to the WAN securely.
-
Network Monitoring and Management:
- Utilize network monitoring tools and management systems to track WAN performance, detect issues, and facilitate proactive troubleshooting.
-
Compliance and Regulations:
- Ensure that the WAN complies with industry-specific regulations, data protection laws, and security standards, especially when dealing with sensitive data.
-
Backup and Disaster Recovery:
- Implement backup and disaster recovery solutions for critical WAN components and data. Create a comprehensive disaster recovery plan.
-
Scalability:
- Design the WAN to accommodate future growth by considering additional sites, increased bandwidth demands, and new applications.
-
Service Level Agreements (SLAs):
- Establish SLAs with service providers to ensure they meet agreed-upon performance, availability, and support requirements.
-
Documentation:
- Maintain detailed documentation of the WAN's architecture, configurations, and any changes made over time. This documentation is crucial for troubleshooting and future planning.
-
Testing and Optimization:
- Conduct thorough testing of the WAN's performance, security, and failover mechanisms. Continuously optimize the network based on monitoring and performance analysis.
Creating a robust WAN network solution requires careful planning and consideration of various factors, including network architecture, security, performance, and compliance. In many cases, organizations seek the expertise of WAN specialists or consultants to ensure the WAN meets their specific needs and can adapt to evolving technology and business requirements

WiMAX Solution
WiMAX (Worldwide Interoperability for Microwave Access) is a wireless communication technology that provides high-speed, long-range wireless broadband access. It is designed to deliver wireless internet access to homes, businesses, and mobile devices over a wide area.
Here's an overview of a WiMAX solution:
We Provide Complete WiMAX Solution:
- Base Station (BS): The base station serves as the central hub for WiMAX communication. It connects to the wired network and communicates with subscriber stations (SS).
- Subscriber Station (SS): Subscriber stations are the endpoints that connect to the base station. They can be fixed (for homes and businesses) or mobile (for on-the-go access).
- Wireless Backhaul: This connects the base station to the core network, typically through fiber or microwave links.
- Core Network: The core network handles traffic routing, authentication, and service provisioning. It connects the WiMAX network to the internet and other networks.
- Authentication and Security: WiMAX includes security features such as encryption, authentication, and authorization to protect data transmitted over the network.
Key Features and Benefits of a WiMAX Solution:
- High-Speed Internet Access: WiMAX provides high-speed broadband internet access, making it suitable for data-intensive applications, including video streaming and online gaming.
- Long-Range Coverage: WiMAX offers greater coverage compared to Wi-Fi, making it suitable for providing internet access to rural or underserved areas.
- Scalability: WiMAX networks can be easily expanded by adding more base stations and subscriber stations to meet growing demand.
- Quality of Service (QoS): WiMAX supports QoS features to prioritize different types of traffic, ensuring a consistent user experience for applications like voice and video.
- Mobility: Mobile WiMAX (802.16e) allows for on-the-move connectivity, making it suitable for providing internet access to vehicles and public transportation.
- Versatility: WiMAX can be used for various applications, including fixed broadband access, mobile data services, and machine-to-machine (M2M) communication.
Considerations When Implementing a WiMAX Solution:
- Spectrum Licensing: Ensure that the necessary spectrum licenses are obtained from regulatory authorities for deploying WiMAX services.
- Interference: Mitigate potential interference issues with neighboring networks and other radio-frequency devices.
- Infrastructure Deployment: Plan the deployment of base stations and subscriber stations to optimize coverage and capacity.
- Service Offerings: Define the types of services and service plans you will offer to customers, including data speeds and pricing.
- Security Measures: Implement robust security measures to protect user data and the network from unauthorized access.
- Backhaul Capacity: Ensure that the backhaul network has sufficient capacity to handle the traffic generated by the WiMAX network.
- Customer Support: Establish customer support processes to address technical issues and inquiries from subscribers.
WiMAX can be a valuable solution for providing broadband access, especially in areas where traditional wired infrastructure is challenging to deploy. However, it's essential to plan and optimize the network carefully to deliver reliable and high-performance services to customers.
We offer Complete Network Security Solution:
- Firewalls: Firewalls act as a barrier between the internal network and the external world, monitoring and controlling incoming and outgoing traffic based on established security rules.
- Intrusion Detection System (IDS) and Intrusion Prevention System (IPS): IDS detects suspicious activities or potential threats within the network, while IPS can actively block or mitigate those threats.
- Antivirus and Antimalware Software: These tools scan and remove malicious software, such as viruses, worms, Trojans, and spyware, from devices and networks.
- Virtual Private Networks (VPNs): VPNs encrypt data in transit over public networks, ensuring secure communication for remote and branch office connections.
- Network Access Control (NAC): NAC solutions enforce security policies by controlling access to the network based on device health, user authentication, and compliance checks.
- Data Loss Prevention (DLP): DLP tools monitor and protect sensitive data, preventing unauthorized access or transmission of confidential information.
- Email Security: Email security solutions include spam filters, email encryption, and phishing detection to protect against email-based threats.
- Web Application Firewalls (WAFs): WAFs protect web applications from vulnerabilities and attacks, including SQL injection and cross-site scripting (XSS) attacks.
- Network Segmentation: Segmenting the network into isolated zones or VLANs can limit lateral movement by attackers and reduce the attack surface.
- Security Information and Event Management (SIEM): SIEM systems collect and analyze log data from network devices and applications to detect and respond to security incidents.
- Two-Factor Authentication (2FA) and Multi-Factor Authentication (MFA): 2FA and MFA add an additional layer of security by requiring users to provide multiple forms of verification to access network resources.
- Security Policies and User Education: Develop and enforce security policies, and provide ongoing cybersecurity training to employees to raise awareness and reduce human-related risks.
- Regular Patch Management: Keep all network devices, operating systems, and software up to date with security patches and updates to mitigate known vulnerabilities.
- Incident Response Plan: Develop a clear incident response plan outlining steps to take in the event of a security breach or incident.
- Network Monitoring and Auditing: Continuously monitor network traffic, perform security audits, and conduct penetration testing to identify vulnerabilities.
Considerations for Implementing Network Security Solutions:
- Risk Assessment: Conduct a thorough risk assessment to identify potential threats and vulnerabilities in your network.
- Compliance: Ensure that your network security measures align with industry regulations and compliance standards relevant to your organization.
- Scalability: Plan for scalability to accommodate the growth of your network and changing security requirements.
- User Authentication: Implement strong authentication methods, and regularly review and update user access privileges.
- **Encryption
LAN Solution
We Digital Solution Company Design an efficient and robust Local Area Network (LAN) solution is crucial for ensuring smooth data communication and connectivity within an organization. LANs are commonly used for connecting computers, devices, and resources within a limited geographical area, such as an office building or campus.
Here are the key elements to consider when planning a LAN solution:

-
Topology Selection:
- Choose the appropriate LAN topology based on the organization's requirements. Common topologies include star, bus, ring, and mesh. The star topology, where all devices are connected to a central hub or switch, is widely used for its simplicity and reliability.
-
Network Hardware:
- Select network hardware components such as switches, routers, access points, and network cables. Use gigabit or higher-speed switches for faster data transfer rates.
-
IP Addressing and Subnetting:
- Plan the IP addressing scheme for your LAN. Subnetting allows you to segment the network logically, enhancing security and performance.
-
Quality of Service (QoS):
- Implement QoS policies to prioritize network traffic, ensuring that critical applications receive the necessary bandwidth and low-latency connections.
-
Network Segmentation:
- Divide the LAN into segments or VLANs (Virtual LANs) to isolate traffic, enhance security, and improve network management. VLANs are often used to separate departments or functions.
-
Network Security:
- Implement robust security measures, including firewalls, intrusion detection/prevention systems (IDS/IPS), antivirus software, and strong authentication mechanisms to protect the LAN from threats.
-
Redundancy and High Availability:
- Build redundancy into critical network components like switches and routers to prevent single points of failure. Implement High Availability (HA) solutions to minimize downtime.
-
Monitoring and Management:
- Utilize network monitoring tools to keep an eye on network performance and detect issues proactively. Network management systems can help with configuration, optimization, and troubleshooting.
-
Wireless LAN (Wi-Fi):
- If your LAN includes wireless connectivity, ensure proper design, placement, and security of access points (APs). Implement the latest Wi-Fi standards for improved performance and security.
-
Cabling Infrastructure:
- Ensure that the cabling infrastructure (e.g., Ethernet, fiber optics) is installed correctly and is capable of handling current and future bandwidth requirements.
-
Scalability:
- Design the LAN to accommodate future growth. Consider the addition of new devices and services without significant disruption.
-
Network Policies and Procedures:
- Establish network policies and procedures to govern network usage, access control, and data handling. Educate users about acceptable use and security practices.
-
Backup and Disaster Recovery:
- Implement regular backups of network configurations and critical data. Develop a disaster recovery plan to ensure business continuity in case of network failures.
-
Compliance and Regulations:
- Ensure that the LAN complies with industry-specific regulations, data protection laws, and security standards.
-
Documentation:
- Maintain detailed documentation of the LAN's architecture, configurations, and any changes made over time. This documentation is invaluable for troubleshooting and future planning.
-
Testing and Optimization:
- Conduct thorough testing of the LAN's performance, security, and failover mechanisms. Continuously optimize the network based on monitoring and performance analysis.
Creating a well-designed LAN solution requires careful planning, ongoing maintenance, and adaptability to changing technology and business needs. It's often beneficial to involve network experts or consultants to ensure the LAN meets your organization's specific requirements.

Wireless Solution
The innovative wireless solution seamlessly integrates with our existing network infrastructure, providing faster data transfer speeds, improved reliability, and greater flexibility, ultimately enhancing our overall operational efficiency and customer satisfaction.
Here's an overview of a Wireless Solution:
We offer Complete Wireless Solution:
- Access Points (APs): Access points serve as the connection point between wireless devices (e.g., laptops, smartphones, IoT sensors) and the wired network. They transmit and receive wireless signals.
- Wireless LAN Controller: A wireless LAN controller manages multiple access points, ensuring seamless roaming, load balancing, and centralized configuration management.
- Wireless Security: Security measures include encryption (e.g., WPA3), authentication (e.g., WPA3-Enterprise), intrusion detection, and rogue AP detection to protect wireless networks from unauthorized access and attacks.
- Wireless Standards: Wireless solutions operate based on standards such as Wi-Fi (802.11), Bluetooth, Zigbee, and cellular technologies (4G/5G).
- Spectrum Management: To prevent interference, spectrum management ensures that wireless devices operate on non-overlapping channels and frequencies.
- Wireless Controllers and Management Software: Centralized controllers and management software allow administrators to configure, monitor, and troubleshoot wireless networks efficiently.
- Wireless Mesh Networking: Mesh networks enable devices to relay data through one another, creating a self-healing network with extended coverage.
- Guest Access: Guest access solutions allow secure, isolated access for visitors or temporary users without compromising the primary network's security.
Considerations When Implementing a Wireless Solution:
- Coverage and Capacity Planning: Determine the required coverage area and assess the number of users and devices to ensure sufficient capacity.
- Network Topology: Decide between a traditional hub-and-spoke topology or a wireless mesh topology based on your coverage and redundancy requirements.
- Frequency Bands: Choose the appropriate frequency band (2.4 GHz and 5 GHz for Wi-Fi) based on interference levels, signal propagation, and device compatibility.
- Security: Implement strong encryption, authentication, and security policies to protect the wireless network from unauthorized access and attacks.
- Quality of Service (QoS): Prioritize traffic for critical applications, such as VoIP or video streaming, to ensure optimal performance.
- Device Compatibility: Ensure that wireless devices (e.g., smartphones, laptops, IoT sensors) are compatible with the chosen wireless standards and protocols.
- Scalability: Plan for network growth and the addition of new devices by designing a scalable wireless infrastructure.
- Roaming: Ensure seamless roaming for mobile devices by optimizing AP placement and signal handoff between access points.
- Security Policies: Define and enforce network security policies, including access controls, firewall rules, and regular security audits.
- Performance Monitoring: Implement network monitoring and management tools to continuously monitor performance and troubleshoot issues.
- Compliance: Ensure that the wireless solution complies with regulatory requirements and data protection laws, especially when handling sensitive information.
- Backup and Redundancy: Plan for backup power sources and network redundancy to maintain connectivity during outages.
Wireless solutions offer flexibility and mobility for a wide range of applications, from office Wi-Fi networks to industrial IoT deployments. Careful planning, security measures, and ongoing management are essential for a successful wireless implementation that meets your organization's needs.
SD-WAN (Software-Defined Wide Area Network) Solution
Our adoption of an SD-WAN (Software-Defined Wide Area Network) solution has revolutionized our network management, allowing us to dynamically optimize traffic, reduce costs, and ensure a more efficient and reliable communication infrastructure for our global operations.
Here are the key elements of an SD-WAN solution:
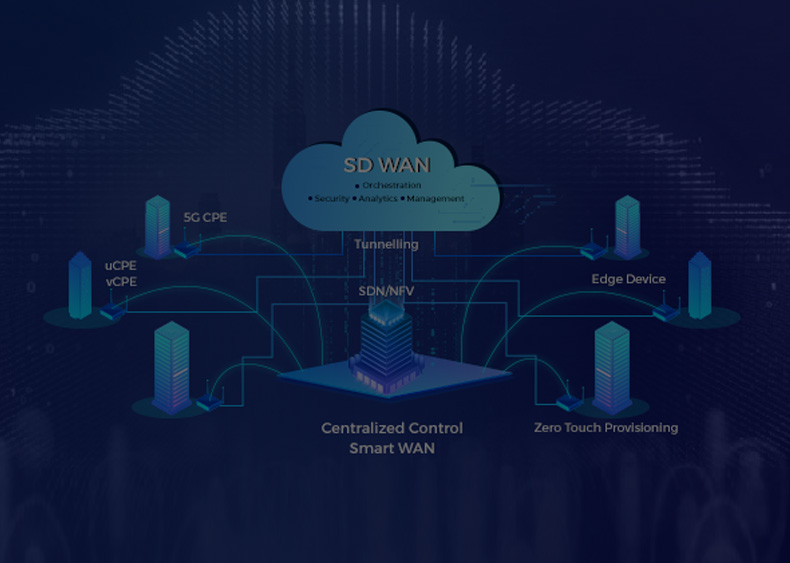
- Components: Includes edge devices, a centralized controller, and various transport options.
- Benefits: Enhances network performance, flexibility, and cost-effectiveness.
- Key Features: Dynamic path selection, security features, Quality of Service (QoS), and WAN optimization.
- Considerations: Business objectives, vendor selection, security integration, traffic policies, testing, and compliance.
- Deployment: Cloud-hosted, hardware appliance, or hybrid approach.
- Migration: Plan migration from existing WAN to SD-WAN with minimal disruption.
- Training: Train IT staff and users on SD-WAN usage and management.
- Support: Establish a support and maintenance plan with the vendor or service provider.
- Outcome: Improved WAN management, application performance, and cost savings.